Side Channel Exploited by My2022 App

Advice to App Users:
- Upgrade to the newest version of the My 2022 app (2.0.8)
Details
Recently, Canada’s Citizen Lab released a detailed investigation of the mobile app provided by the Government of the People’s Republic of China that appears mandatory for all attendees of the upcoming Winter Olympic games. We took a look to see if there was anything else we could find (version 2.0.4, released January 2022), and noticed evidence of a side channel being exploited. In particular, we found that the MAC address of the mobile device is being sent to the domain “bigdata.beijing2022.cn”. Specifically, they send a base64-encoded gzip-compressed JSON-object, which contains the MAC address in a field called “properties.$ios_install_source”; a pretty-printed and redacted version of it is below.
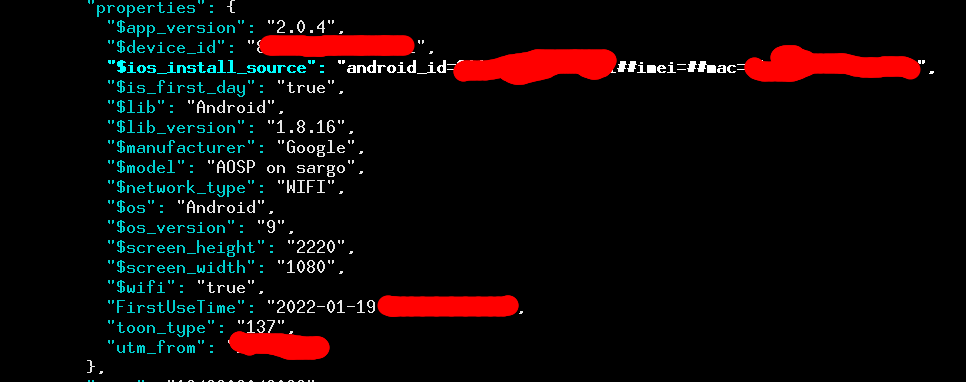
A MAC address is a unique serial number attached to each piece of networking hardware. They are assigned by the manufacturer when creating the hardware and remain fixed to the device, making them ideal persistent identifiers—they never change. (See our other blog post on tips for developers to avoid using MAC addresses.) Data collectors collect MAC addresses because they are persistent and inescapable (i.e., consumers can’t easily reset them, unlike clearing a web browser’s cookies). Even a factory reset of the phone won’t change it! It is exactly for this concern that Google has, since 2015, disallowed the collection and use of device MAC addresses by mobile applications.
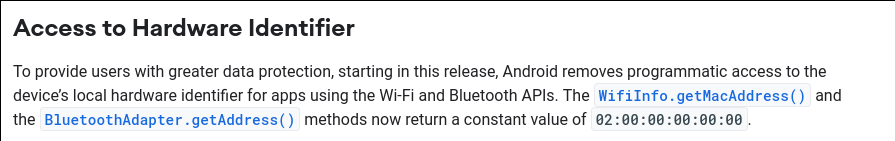
Unfortunately, MAC addresses were never designed to be hidden, because they were never intended to be used for invasive tracking. For this reason, a number of different side channels existed on Android that app makers have found and use to circumvent the permissions system. When we find such issues, we responsibly disclose them to Google. For example, Tiktok exploited a Java networking configuration data structure, and Unity exploited low-level input-output controls to get this data. Another SDK, called devtodev, was accessing MAC addresses via C++ code using the getifaddrs() system call, which ultimately is the same path that the Java networking configuration goes through. While these issues are all fixed in Android version 11, it remains exploitable on older versions of Android, as well as apps targeting a lower-version SDK. This means that many users are still vulnerable, if they don’t have a state-of-the-art phone capable of running the most-recent version of Android.
Our investigation found that the Java networking interface API was the method used to get the MAC address. We’ve seen many others apps collecting the MAC address in this exact same way over the years, and this motivated us to write a developer-targeted document about why that shouldn’t be done. But the fact that users—Olympic athletes—are compelled to use this app motivated us to report this new finding to Google. While older versions of the operating system cannot easily be patched to remove the vulnerability, we are pleased that the developer of the My 2022 app has now updated it, and as of version 2.0.8 (released early February, 2022), we no longer see collection of the MAC addresses.